SHORT: CrowdStrike has a secret…
 In addition to global IT outages, CrowdStrike is involved in political nonsense.
In addition to global IT outages, CrowdStrike is involved in political nonsense.
Surprise, surprise…
I’ll give you a hint: Russia, Russia, Russia!!!
Another hint: Orange Man Bad!
 In addition to global IT outages, CrowdStrike is involved in political nonsense.
In addition to global IT outages, CrowdStrike is involved in political nonsense.
Surprise, surprise…
I’ll give you a hint: Russia, Russia, Russia!!!
Another hint: Orange Man Bad!
 The global IT outage on Friday, July 19th 2024 was a humdinger.
The global IT outage on Friday, July 19th 2024 was a humdinger.
We’re told it’s nothing to worry about, but what’s really going on?
I’m afraid the rabbit hole goes a bit deeper than you think.
Join me for a look at the Crowdstrike “bug” and what it means for you…
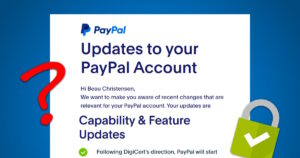 If you have a PayPal account – and especially if you’re selling anything and getting paid via PayPal – then you’ve no doubt received a strange e-mail (or ten) recently.
If you have a PayPal account – and especially if you’re selling anything and getting paid via PayPal – then you’ve no doubt received a strange e-mail (or ten) recently.
In short, you’re supposed to add the DigiCert Global Root G2 Chain to your “trusted store”.
Bad things will happen if you don’t!
More stuff to fix, right? Not so fast…
What’s really going on here?
 Ah, the eternal battle: iOS or Android?
Ah, the eternal battle: iOS or Android?
These days, there’s a big war going on where both sides are trying to prove that their mobile OS is the safest and most privacy-friendly.
So, which is it?
Join me for a deep dive into the wonderful world of smartphones…
 Even if you don’t know the term ‘phishing scam’, chances are you’ve already been targeted by many of them.
Even if you don’t know the term ‘phishing scam’, chances are you’ve already been targeted by many of them.
A phishing scam is when someone uses a genuine-looking e-mail, login page, SMS, or whatever to fool you into giving up personal data – like logins, passwords, card and banking info, etc.
They often involve some kind of ‘hook’ that makes you worried or scared. When that happens, you stop thinking and fall into the trap.
But these scams are very easy to avoid with a bit of extra attention. I’ll show an example of a phishing scam I received recently and then take it apart piece by piece so that next time, you’ll know exactly what to look for to protect yourself!
It’s so incredibly useful, and at the same time you won’t find a more wretched hive of scum and villainy. Well, technically, it’s more useful than villain-y.
Still, it’s good to be careful!
So what’s the best way to stay safe when using the internet? Strong passwords? Antivirus? Browser add-ons? Privacy enhancers? VPNs?!
That’s all well and good, but there’s one trick that will never let you down…
 It’s everywhere these days: 2FA (two-factor authentication).
It’s everywhere these days: 2FA (two-factor authentication).
More and more, you must use something more than just a password to secure your online accounts.
Some sites, like PayPal, are apparently requiring 2FA for everyone.
So, what types of 2FA are there? Do you have to use a smartphone? Is there an alternative to SMS-based 2FA? And most importantly, is it that much safer?
Finally, I reveal the other reason why everyone is pushing 2FA so much – and it doesn’t have anything to do with your security or privacy!
As regular readers know, I’m not a big fan of the traditional smartphone craze.
Sure, they’re really handy gizmos, but the amount of data being hoovered up and shipped off to large service providers is a bit frustrating.
As if things aren’t bad enough on that front, it gets better! It turns out that even individual APPS running on your phone are spying on you – specifically, they’re tracking your location (among other things).
What’s more, your location data can be easily linked to you as a private individual. To top it all off, this data is bought and sold to anyone who will pay – and all in the blink of an eye!
 I’ve been using dumbphones for awhile now, but I started to miss some smartphone features.
I’ve been using dumbphones for awhile now, but I started to miss some smartphone features.
Then a friend of mine mentioned LineageOS again. I decided to take the plunge… And I’m glad I did!
It IS possible to have a relatively private smartphone without all the Googley madness – even in this day and age.
But it does take a bit of time, patience, and some technical know-how.
Note that I don’t walk through the entire installation process here since it’s particular to your specific phone…
 In a shocking revelation that simply re-affirmed what everyone already knew, the 9th US Circuit Court of Appeals again ruled that internet platforms have nothing to do with the First Amendment because they’re private corporations.
In a shocking revelation that simply re-affirmed what everyone already knew, the 9th US Circuit Court of Appeals again ruled that internet platforms have nothing to do with the First Amendment because they’re private corporations.
Well, duh!
In a ruling on February 26th, the court said that, “merely hosting speech by others is not a traditional, exclusive public function and does not alone transform private entities into state actors subject to First Amendment constraints.”
Can’t say I didn’t see that one coming – again…
Recent Comments