This article originally appeared in Issue #13 of The Dot Connector Magazine.
Whether it’s the “Iranian Cyber Army”, those darn “Chinese Hackers”, or just your average script kiddie, everyone is aware that there bad people out there who want to mess with your glorious internet surfing experience.
You probably have heard of things like DoS (Denial of Service) attacks, and you’ve most certainly heard about viruses, trojans, and worms. But there is one thing I’m betting you haven’t heard much about: DNS cache poisoning.
You’ll see why this is a very important type of attack to be aware of a bit later. First, I should probably cover a few basics in case you aren’t a techie nerd. Just for the record, nerds don’t wear coke bottle glasses anymore; they wear contacts. Junk food is out, and healthy eating is in. Flannel shirts? Yes. Pocket protectors? No. And contrary to popular belief, we are generally good-looking. It’s all part of Nerd 2.0.
But, I digress.
DNS stands for Domain Name System. There is a network of DNS servers that make up part of the internet. The purpose of these special servers is to translate domain names (like thedotconnector.org or www.sott.net) into IP addresses so that you can find what you’re looking for. Each computer on the internet, whether it is a server or your personal computer, must have an IP address that looks something like this: 212.113.132.182
Well now, how would you like to remember “212.113.132.182” instead of “TheDotConnector.org”? You wouldn’t! That would be insane. Thus, domain names were born, along with Domain Name System servers. DNS servers translate an easy-to-remember name into a not-so-easy-to-remember IP address. Once that has happened, your computer knows the IP address of the server to which it should connect. Just think of domain names as “The Johnson Family” and the corresponding IP address as the family’s actual street address.
There are many DNS servers connected to the net. They form a sort of gigantic distributed database of domain-name-to-IP-address records. When you want to load a web site, your computer connects to your local DNS server, which checks to see if it knows the web site you want. If it doesn’t, it contacts other official, higher-level DNS servers to see if any of them know where the Johnsons live. Eventually, some DNS server out there somewhere says, “I know! They live at 123 Elm St. in Happyville, Wisconsin!” This (IP) address is passed back, and your local DNS server will then store, or cache, a new record of the location. Your computer itself even temporarily caches some of this information. That way, when you click a link on a web site, the whole lookup process doesn’t have to be repeated.
As you can imagine, the DNS isn’t exactly simple. There’s a LOT more to it than I have described here, but that’s all you really need to know in order to understand a DNS cache poisoning attack.
[ad name=”square-l”] Now we get to the fun part. Each time DNS lookup data is exchanged between servers, a Top Secret Code is used to make sure that someone isn’t trying to pull any funny business. Imagine what would happen if someone could guess that top secret code and thereby hijack your web browsing! If someone was able to reply to your DNS lookup request and make it look like an official DNS server response, they might be able to report back that the Johnsons live in Australia instead of Wisconsin. And then you’d be in BIG trouble because you really wanted Mrs. Johnson’s world famous apple pie recipe.
This type of fake response is exactly what happens with a DNS cache poisoning attack. And here you thought it was going to be hard to understand!
The “secret code” used to make DNS transactions secure is more or less a random number. Unfortunately, computers cannot generate truly random numbers – they have to use tricks to generate “almost random” numbers. And therein lies the rub: a smart hacker knows how to essentially “crack the code” so that he will be able to guess what top secret code is being used.
But alas, this code guessing takes a certain amount of trial and error. If Mr. Hacker doesn’t hurry up, the real DNS server will send its official response back to you, and you’ll know exactly where the Johnsons live. Somehow, Mr. Hacker needs to slow down the DNS server he is attacking so that he can send his fake response back first.
Enter the DoS attack! While attempting to hack the top secret code, Mr. Hacker also sets up a denial of service attack on the DNS server. Perhaps Mr. H has a “botnet”, which is just a fancy way of saying, “a bunch of computers that are hijacked to do evil things”. Mr. H will use his Evil Computers to bang away on the door of the DNS server. Simultaneously, he tries to guess the top secret code. Since he has slowed down the DNS server, Mr. H can successfully crack the code, generate a fake DNS response, and send it back to you before the official DNS server gets around to sending its genuine reply.
Here is the key: Remember how I mentioned that DNS servers cache lookup responses? Well, if Mr. H sends a fraudulent response that looks genuine (since he has cracked the top secret code), other DNS servers will cache this erroneous info and start sending it out to other surfers who use the same DNS servers as you. Oops. That is why the attack is called “DNS cache poisoning”.
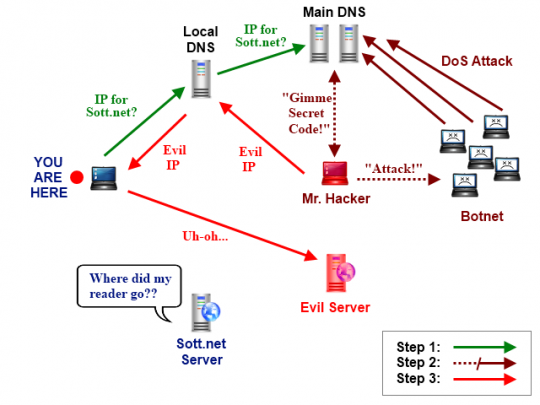
So, that’s great… but what does it mean practically speaking? A picture is worth a thousand words:
As you can see, the whole point of a DNS cache poisoning attack is to make you think that you are looking at “Sott.net”, when in reality you are downloading whatever data is found on the Evil Server with a different IP address. Your web browser will still show “Sott.net” in the URL bar, but the data is not coming from the real Sott server.
Now, if you are like Hercule Poirot, your little grey cells will be working feverishly as you realize the full implications of this terrible tragedy. It may look like your favorite web site has been hacked, when in fact there is nothing at all wrong with it. You have simply been fooled into thinking that your favorite site has been hacked. That alone is pretty evil…
But consider the following possibilities:
- The Evil Server contains malware that it sends to your computer
- The Evil Server presents you with a web site that looks like the real site, but contains false or defamatory information. Thus, you think the owners of your favorite site have gone bonkers. Not very nice, is it?
- The Evil Server itself actually connects to the real server, gets the content you want, and then passes it back to you. As far as you are aware, you’re simply surfing like normal and the web site is fine – but Mr. Hacker is able to see all the data transmitted since it’s all being routed through his Evil Server! Things like bank information, credit card numbers, logins, passwords, and any other kind of info can be stolen in this way. This is called a “Man in the Middle” attack, and it is perhaps the most diabolical use of DNS cache poisoning. You don’t even know that your data has been stolen.
What can you do to protect yourself?
Fortunately, the problem of DNS cache poisoning is being addressed with continual improvements to the DNS system – although I would argue not quickly enough. It used to be that the top secret code that DNS servers used was linear. In other words, the “top secret” code was generated like this: 1, 2, 3, 4, 5, and so on.
Yeah, I would so fire the person who came up with that idea! Definitely not Nerd 2.0…
Today the top secret codes are “random”, but that is now not quite good enough, and so things are changing again.
Unfortunately, there is not much that you or the people who run your favorite web site can do about this type of attack. The responsibility lies with service providers and hosting companies. Most are on the ball, but even the news web site, Sott.net, has been the target of DNS cache poisoning attacks on multiple occasions (which, as the Chief SOTT Techie, I found rather annoying). Since then, it appears that some changes have been made at the hosting company’s end to minimize attacks.
Like viruses, malware, and other types of attacks, the attackers will always work at coming up with new ways of screwing things up, and so providers and end users must always be aware of the modes of attack and how to thwart them.
Fortunately, you can at least know what is happening when such an attack occurs. Find out the IP address of your favorite web site, and write it down. You can do this using various tools. For example, there are add-ons for Firefox, like ShowIP and Flagfox, that will show the IP address for every site you visit. Or, you can open a command prompt and simply type:
ping somewebsite.com
The results will display the web site’s IP address. Make a note of the IP address, and if you suspect an attack at a future date, repeat the IP lookup process. If the IP address has changed and there appears to be something fishy with the site itself, it may be a DNS cache poisoning attack. Just remember that sometimes, a web site’s IP address will change for perfectly valid reasons.
In the end, you can’t know 100% if in attack is occurring. But at least now you are aware of exactly how such a DNS attack occurs, and you have some basic tools at your disposal to protect yourself.
Happy surfing!





Hi Scottie, great article. Out of interest why did you use Sott.net as an example domain name? It seems like a conspiracy theory website.
Because I’m the sysadmin and webmaster of Sott.net. Keep reading!