 If you have a PayPal account – and especially if you’re selling anything and getting paid via PayPal – then you’ve no doubt received a strange e-mail (or ten) recently.
If you have a PayPal account – and especially if you’re selling anything and getting paid via PayPal – then you’ve no doubt received a strange e-mail (or ten) recently.
In short, you’re supposed to add the DigiCert Global Root G2 Chain to your “trusted store”.
Bad things will happen if you don’t!
More stuff to fix, right? Not so fast…
What’s really going on here?
The Message
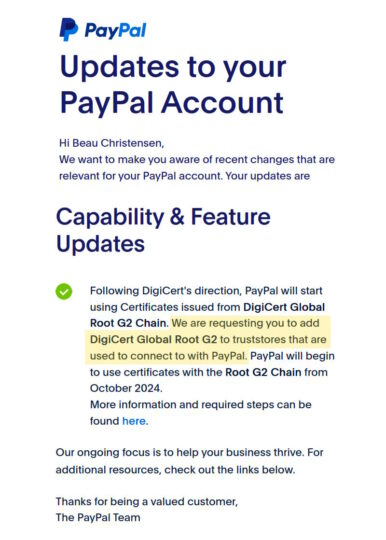
The message will look something like this:
If you click the link, you can read a confusing explanation about SSL certificates and trusted chains. Even better, that page kinda says you still have over a year to make whatever change is needed. So, no rush? Or panic?
No Rush – at all
The truth of the matter is that this is very much a big stink over absolutely nothing.
What do you need to do? Most likely, nothing. Nada, zip, zilch!
What IS a root certificate?
Simply put, all the encryption you use without thinking about it, like viewing websites over HTTPS, is done via cryptographic certificates. Some company/authority has a root certificate. From that root, an intermediate certificate can be made, and so on down the line until we reach the SSL certificate that actually secures an HTTPS-served web site.
Each certificate level is verified that its safe to use by using the certificate above it – all the way back up to the root certificate. It’s just a pyramid structure, with the root cert at the apex. So yeah, root certs are kinda important.
The now-infamous G2 cert
The “G2” root certificate isn’t new. In fact, it was added to most linux distributions way back in 2014 – TEN YEARS AGO!
The same is true for Windows. New certs are generally delivered and installed on your devices in OS and program updates – automatically! You never have to think about it. Been that way for a LOOOONG time…
Some people have suggested that Windows 7 may not have this new root certificate, but that’s unlikely given that Windows 7 support officially ended on January 14, 2020 – over 6 years after the G2 cert appeared.
Once your OS is no longer updated, you won’t get any new root certificates – most likely. But any browser, for example, that you keep updated on your machine WILL have them – most likely.
This is one good reason why I tell people to keep their OS, browser, and mail client updated. Eventually, stuff just stops working, very often due to expired root SSL certificates.
You can check yourself by doing:
- Start button
- Type: certificate
- Click: Manage computer certificates
- Double-click the Trusted Root Certification Authorities folder
- Double-click the Certificates folder
- Oh look:
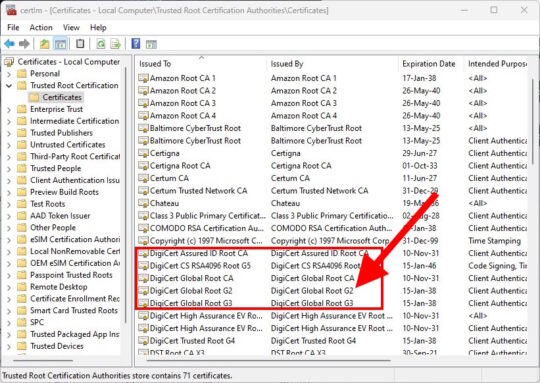
Um, it looks like I already have DigiCert Global Root G2, G3, G5, etc! This is my surprise face: 😐
But what about my web site’s SSL certificate?
What, indeed?
Chances are, that’s already done, too. YEARS ago, I was informed that I needed to generate a new SSL cert for one site I manage, free of charge. It was for this very reason…
So, I did it – YEARS ago.
In summary: Somebody’s fired!
So yeah, I have NO idea why PayPal is sending this message out, thereby making everyone freak out.
It’s completely unnecessary.
Just keep your devices up to date. If you purchased an SSL certificate for a hosted web site, your hosting company will take care of it for you – or tell you exactly what you need to do (if anything).
And if you bought a standalone SSL cert for, say, a dedicated server, your SSL provider will also tell you what you need to do. Done.
The only case I can think of is if you have some kind of standalone, self-contained app with its own certificate store, then you might need to add the G2 root cert. But even that seems rather unlikely given that it’s been around for 10 years already!
In any case, PayPal is literally the last company on earth that should be telling you about this stuff.
So, somebody’s fired!


gracias amigo
Could you ELI5 how the cert pyramid can have multiple paths? I ran into a cert problem where one of the paths was expired and the workaround was to manually remove the expired one to force use of the other path.
“This means that clients verifying certificate chains can find the alternative non-expired path to the ISRG Root X1 self-signed certificate in their trust store.
Unfortunately this does not apply to OpenSSL 1.0.2”
https://www.openssl.org/blog/blog/2021/09/13/LetsEncryptRootCertExpire/
Or, they are getting people ready for when they have to update to CBDC