 You may have heard of browser fingerprinting and its security implications. Then again, maybe not.
You may have heard of browser fingerprinting and its security implications. Then again, maybe not.
In either case, you probably haven’t heard the whole story.
A browser fingerprint is when, by visiting a web site, that site can generate an ID (or fingerprint) that is unique to your computer. The fingerprint can then be sent to their server, and you can be tracked.
No cookies required, no security holes required, no “Do not track me” setting can make a difference… Just plain old browsing the web will do it!
Okay, so how does this all work? And what does it mean?
First, what it means
Even if you prevent sites from storing cookies on your puter, sites and ads can still track you. In fact, anybody can track you. In fact, you can pretty much take it to the bank that right now, when you browse the web, God, the NSA, and everyone’s dog is already using browser fingerprints to track you. It’s a marketing and intelligence dream come true!
There is no catch, really. Even if you disable Flash, you can still be tracked. If you disable Java, you can still be tracked. If you disable JavaScript, it gets a lot harder. Most of the well-known techniques of browser fingerprinting are done via JavaScript.
Trouble is, practically every web site on the planet requires JavaScript these days. JS is what makes Google Maps work, and Facebook, and Gmail, and everything else. Turn off JavaScript, and you’re pretty much browsing in the stone age. In short, you CAN’T turn off JS if you need to use anything on the internet. NoScript? Well, sure, it might block JS on unknown sites, which might protect you a little. But, like I said, JS simply makes the internet go these days.
How does it work?
It’s pretty simple… Surprisingly so, actually.
You load a web site. Part of the JavaScript content your browser downloads from the web site is a tiny bit of code that runs on your computer, just like JavaScript normally does. Except instead of drawing a pretty map, or showing your mail, it simply reads and computes and tests a few things in your browser.
 For example, it’s a total breeze to query your browser and find out things like:
For example, it’s a total breeze to query your browser and find out things like:
- What OS you’re using
- What browser you’re using
- What plugins you have installed
- What time zone you’re in
That’s the kiddy stuff. This is all stuff that is supported by every major browser out there, and it’s built in to JavaScript/your browser – and has been for quite some time now.
Where it starts to get fun is the browser plugins…
Using a very simple chunk of JS, I can see what plugins you have installed. Does your browser support QuickTime? VLC media player? RealMedia? Acrobat? Foxit? Video streaming of various flavors?
Well, that doesn’t seem like it would be a big deal. After all, doesn’t everybody use that stuff? Yes and no.
Not everyone has the same plugins. Not everyone has the same versions of those plugins. On different browsers or OSes, the plugin information will be different. This all contributes to the uniqueness of your browser.
So, gimme an example
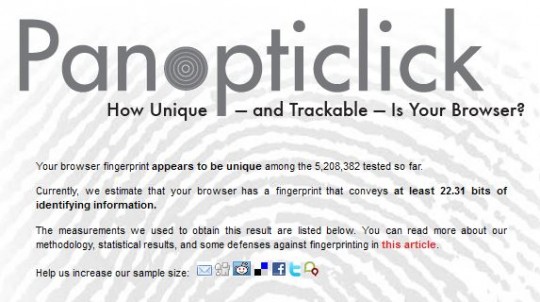
Okay, go here: https://panopticlick.eff.org. Click the Test Me button. You can ignore the Flash and Java prompts. They aren’t needed.
You’ll probably see a message like:
You’ll also see a table of results.
The first column shows what information was queried via JS. The second column shows the estimated bits of identifying information gleaned, and the third column shows that the info obtained makes you unique in 1 out of X people.
For example, my plugins info alone means that my browser is unique in an estimated 1 out of over 5.2 million others tested. That’s a helluva lot of information right there!
What does this “bits” thing mean, though?
Well, think of it this way: 33 bits of information represents 8,589,934,592 different possibilities (233 = 8,589,934,592). Thus, with 33 bits, we can uniquely identify you out of 8.5 billion others – which is more than the people on Planet Earth.
Now, you’ll notice that the Panopticlick site probably tells you that you’re only somewhere around 22 bits of info. “Oh, thank god, I’m safe!”
Not so fast…
The combination of identifying tricks are estimates, as Panopticlick is a “research project” of the EFF (Electronic Frontier Foundation). When you read the fine print, it very quickly becomes clear via simple common sense that their estimates of uniqueness are most certainly rather conservative. Naturally, they don’t want to help the bad guys…
The methods they use for testing are also just the tip of the iceberg.
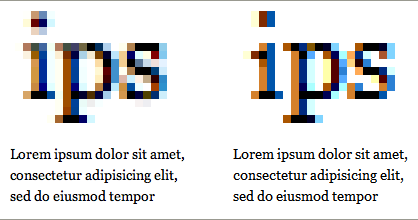
There are other techniques, such as the Canvas test. There is also a JS-based font-rendering test. There is also a WebGL test. In short, I write a bit of JavaScript, and your browser creates a “hidden” box on the web site where it renders fonts, graphics, etc. By doing this, and then converting the hidden output into raw data, I have a LOT of information. Why?
It turns out that there is a very high probability that your computer will not render text or graphics or whatever the same way my computer does. You have a different graphics chip, different hardware, different software versions, different drivers, different browser, etc. This all adds up so that the way an “A” (or a goat) is rendered on your puter is NOT the same as the way an “A” (or a goat) is rendered on mine. This makes our 2 puters unique from each other.
Canvas tracking alone has been described by some as so precise that a better name would be “Browser DNA Testing”.
As I said, this is all extremely easy to do. And, because I was seriously annoyed at the “watered down-ness” of the Panopticlick info, I did some further research. I wanted to know exactly how bad this whole browser fingerprint thing is. If it’s bad, I want to know:
How deep does the rabbit hole go?
Well my friends, it’s frickin’ deep.
I took a popular JavaScript-only fingerprint function and modified it quite a bit, adding several other key “goodies”. Then I tested it. Now, my testing methods and statistics are certainly not as broad and thorough as those of the EFF project Panopticlick. But, based on their results, and several other result sets from other fingerprinting experiments (there are quite a few), plus what I learned and how I implemented my own fingerprint scheme, I can say with a very high degree of certainty (98%) that my combination of fingerprint techniques would easily uniquely identify everyone on the planet.
In short, if a single fairly smart dude like me can whip together a fingerprinting function in a day’s work that blows Panopticlick out of the water, then what the hell do you think the alphabet soup agencies and corporate advertising wizards are doing with such toys?
But wait, there’s more…
Did you know that – even though it’s supposed to be disabled now – I can still see whether you’re on a desktop or laptop computer from JavaScript alone? I know what OS you’re using, the type of device (smartphone, tablet, or puter), what browser you’re using, I know the resolution of your screen, I know how big your browser window is (maximized, or not?), I know what time zone you’re in, what your native puter language is set to… I even know if you’re holding your device in portrait or landscape mode.
Hell, with a bit of extra testing, I can even tell with a very high degree of certainty if you have MS Office installed or not – and even which Office applications are installed. I can also tell if you have a GPS device that you update via the web, for example. Lots of products use browser plugins to make the device-web interface very friendly for updates and such. If you’ve got ’em, most likely I’ll know it.
Okay, lots of people might have Office or a GPS of a certain brand, that’s true. But it’s highly doubtful that they’ll also have the exact same plugin info, for example… You can see how this data quickly adds up to a unique fingerprint. When you have multiple sources of info to work with, uniqueness is practically guaranteed.
Now, not all of the information above is technically useful for uniquely identifying someone (this is intentional), but it could be. It’s fairly basic info, but it’s great food for thought. There is a LOT more. When you put it all together, then it’s easy to see that with browser fingerprinting, you are absolutely unique and trackable on the internet.
An analogy or two
 It’s like tracking all the people who drive a black sedan. Well, lots of people drive black cars, right? Sure. But how many have a “Jesus loves You” bumper sticker? And of those, how many have alloy wheels of a certain style? And then on top of that, how many have tinted rear windows, or that stubby little GPS antenna on the roof, or the deluxe stereo system, or…
It’s like tracking all the people who drive a black sedan. Well, lots of people drive black cars, right? Sure. But how many have a “Jesus loves You” bumper sticker? And of those, how many have alloy wheels of a certain style? And then on top of that, how many have tinted rear windows, or that stubby little GPS antenna on the roof, or the deluxe stereo system, or…
Or, it’s like in Hollywood movies when the alphabet soup “good guys” narrow down a search… “Gimme all the black sedans purchased in the past eighteen months, and look for somebody who got a speeding ticket, and cross-reference that with overdrawn bank accounts, for anybody who’s last name starts with the letter M… There! That’s our guy.”
You get the idea. It’s not the significance of ONE source of information from your browser that is valuable; it’s the combination of the bits of data. And then, what if I’m an intell spook, and I know you use a certain ISP? Right there, I’ve excluded tons of users, and greatly minimized the number of bits of information I need to uniquely identify and track you. Oops.
It doesn’t matter if you’re using Private Browsing. You’re still trackable. In fact, if I’m tracking you, and you switch to Private Browsing mode, I may even be able to line up the data side-by-side and realize that you just switched to Private mode to try to foil me!
The point is…
This is just me. I’m not tracking you. I’m just trying to inform you. But if I can pull this off, then you can imagine what the BWB (Bozos with Budgets) out there are doing with it. And, at the moment, there isn’t a damn thing you can do to protect yourself. Go ahead and fake your User Agent… Block cookies… Stand on your head if you want… It really doesn’t matter.
And the so-called “fingerprint-proof” addons/extensions available for popular browsers are basically useless since they don’t protect against all the fingerprinting techniques. In fact, having such an addon installed means I may have another chunk of info to track you with, because that might make your browser more unique!
Are you ready to cry yet? As with most things, it’s not what you do know that can hurt you; it’s what you don’t know.
What exactly are you using for your fingerprint?
No dice. I didn’t create my fingerprinting function to play NSA. I created it to see what was possible, and HOLY COW I nearly fell off my chair… My little experiment is a proof of concept. And yeah, it works… Too well.
But now, I know what’s possible. And now, so do you.


I always knew something was up that they could still track you now i know i was always right, the government the script kitty hackers and alike can see your every move, the internet someday will be the downfall of all of us.
@Tony
thanks for the write up 🙂
I wondered how will your screen resolution help them track down are there any methods like check list to track a person with a IP
many people have the same screen resolution as me how can they track like to hear back from you
It’s just yet another bit of data to add to the mix. It’s not that screen res alone is enough, but rather screen res in combination with all the other data points. For example, screen res + time zone + Flash plugin installed + … and so on.
Now, here’s a fun one for you: JavaScript can more or less me the size of your browser window. So, some people use their browser fullscreen, but others don’t. More data!
Hello Scottie,
I just read your literature on Certificate, passwords and Fingerprints.
Great pieces of research and on top of that written with good old Humour.
Thanks a lot for all your work and info which is revealing of the lack of privacy we indulge in.
Peace